by: Elena Garrett
Augmenting your patch management strategy
According to Microsoft Security Report 2017, hackers and malicious intruders know that nearly all organizations are vulnerable, and often first reach for the lowest-hanging fruit: exploitable weaknesses in legitimate applications. Nearly 21 thousand vulnerabilities for wired and wireless devices were identified in 2017 alone, and a large number of them will trigger a patch of some soft to be issued. With so many vulnerabilities to secure, patching is a daily reality of many IT teams. Yet, patching does not need to be the only strategy to prevent exploitation. We recommend that you supplement your security strategy with measures that address situations when patches do not solve the issue or cannot be applied in a timely manner.
The problems with patches.
- There are too many vulnerabilities on the network to keep track off, with patches for Windows machines being only one part of the problems.
- As important as they are, patches can introduce unexpected service disruptions that can last for days or even weeks, making many network administrators weary of applying new patches immediately.
- Many vendors are slow with providing patches even if the vulnerability is widely known and carries a high risk potential. For legacy software, the support might have ended entirely.
- Some of the most vulnerable software on the network is often part of the architecture for other programs (for example, Java, Apache, various parsers) and those patches cannot be applied without first understanding and mitigating the impact on the other software components.
Although ESP was not designed to be a patch management tool, it can enhance the traditional patch management techniques in several ways:
- Verifying the patches are indeed properly applied
- Performing registry lookup to make sure the proper registry entries have been created
- Creating software-specific, OS-specific, service pack-specific, patch-specific, or even component-specific security policies that could address specific vulnerabilities
- Gathering machines with missing security patches into groups that can be closely monitored or segregated without having to make any changes on the network itself or having to reconfigure any perimeter firewalls.
Best patching practices.
As one of the articles in CSO magazine suggests, unpatched and outdated software continues to be a one of the top targets for cyber criminals. Meanwhile, IT teams struggle to stay current with updates for all the various software (especially non-Microsoft software) that is running on their networks. As one of the most important tips for prevention of a successful cyber-attack, they recommend focusing on applications (Java, Flash, Apache, etc) that are most likely to be exploited, and patch those applications thoroughly and often. They also recommend avoiding software vendors with reputation for slow patch delivery.
We would also recommend that you supplement your patch management strategy with several additional tactics, such as
- continuously monitoring your network for presence of machines with missing critical patches,
- using host risk and value assessment to identify machines that need most care and attention,
- establishing OS-specific or application-specific security policies to proactively mitigate vulnerabilities for which the patches may not be available (or effective).
Timely and effective patching is the ultimate goal of every IT department. But when realities of modern networks (and limitations of software vendors) interfere with the plan, you can proactively integrate additional solutions, such as ESP, in order to add another level of protection to your network.
Delayed Patching
Microsoft patches are issued on a fairly predictable and regular schedule. Other software, especially open-source software, are an entirely different matter. Some older frameworks and applications are still widely used but no longer supported. Many customized applications may require a partial re-write in order to upgrade them. Sometimes the slowest and the most difficult-to-patch components are those that are an integral part of the larger system architecture. One of the worst offenders are usually Java components, content management systems (like Drupal), Apache server functions, scripting platforms, as well as various parsers, converters, and query tools. In this article on top 10 security vulnerabilities of 2016, Java-related frameworks and scripts were listed among the most vulnerable. However, patching those vulnerabilities can present a serious challenge. Applying a patch (even if one is available) may not be desirable at least until all possible side effects of the changes are understood.
In those situations, it may be more beneficial to remedy the vulnerability, at least temporarily, though alternative methods, such as consistently monitoring the machines for suspicious or abnormal activities, changes in configurations or changes in the list of running services. If the vulnerability involves ex-filtration of data or remote access to data, stricter network access policies could be established to help reduce the risk of successful exploitation of that vulnerability.
Ensuring secure settings after gold image installation.
If your organization needs to deploy a large number of physical or virtual hosts using a gold image, you might discover that even though the service pack on the gold image is up to date with Windows updates, the image is missing all the security fixes that were installed on the prior service packs. Performing recursive updates to get all the prior security fixes onto the new machines can take time, effort, and a lot of network bandwidth. In the meantime, what can be done? This is when ESP dynamic grouping of hosts can help. Simply group together all hosts that are missing the most important security fixes, and create a custom communication policy to limit their ability to access ports or IPs that are not required in their normal function. Once all the critical patches are applied to a machine in question, the machine will automatically transition out of the custom group, and the communication restrictions will be removed automatically.
Making the most of your patching efforts
Using ESP hosts risk and value scores to know what needs attention.
IT teams are often faced with shortage of time, staff, or other resources. When faced with those constraints, it is important to make the most of every day spent on patching.
One of the unique features of ESP is the ability to dynamically adjust hosts' risk and value scores based on the type and volume of hosts' activities, membership in various custom groups, and adherence to established security policies. IT teams using ESP could use hosts' risk and values scores to identify highest-priority machines that could account for larger share of vulnerabilities. Those machines could be devoted more time and watched more closely than machines with lower risk or value to the organization.
Checking for presence of correct registry values.
For some updates, Microsoft might require creation of a registry key to patch the vulnerability. For example, in the case of Credential Security Support Provider protocol (CredSSP) Remote Code Execution Vulnerability (CVE-2018-0886), in the patch released on March 20, 2018 it is stipulated that “mitigation consists of installing the update on all eligible client and server operating systems and then using Group Policy settings or registry-based equivalents to manage the setting options on the client and server computers." The key that needs to be created is:
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters with the value: AllowEncryptionOracle and must be present for the proper security setting to be activated.
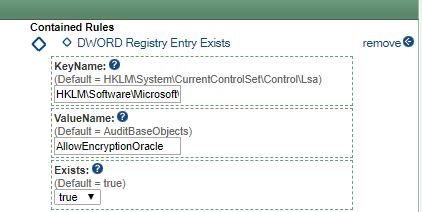
Verifying that the correct key and key value are actually present (instead of assumed to be present) on various machines that may need authentication via CredSSP can be difficult and time consuming without proper software. Again, ESP can help by providing effortless visibility into the network. A policy can be created to check all machines for the presence of the required DWORD entry. Those machines lacking the entry can be easily grouped together in a custom ESP group. The group can be assigned a certain risk coefficient and a custom policy can be created to track or restrict its activities on certain ports. Once the proper registry entry is created on the machines, those restrictions will be removed automatically. Alternatively, ESP could be used to create the required registry key on the machines. Although ESP was not designed to be a remote registry management tool, it has the capabilities to create registry keys and set the proper key values on the managed machines remotely. This could come handy if machines cannot be physically accessed or if Group Policy cannot be used to manage certain settings.
Patch is applied but the vulnerability is still present.
Although most vulnerabilities can be addressed with a single patch, on some occasion multiple patches have to be developed, tested, and installed before the machines are no longer susceptible to risk of an exploit. In those cases, the machines on your network may be fully patched but still vulnerable. ESP can help by providing deep visibility into network traffic and active running processes on the hosts. In case of a specific vulnerability, presence of a running process can be tracked, automatically detected, and automatically assigned custom security policies designed to contain ex-filtration of data or communication with outside IP addresses.
Updates that cannot be viewed via View Installed Updates.
Normally, we would access the list of installed Windows updates using Programs and Features → View Installed Updates or by using the command line
dism.exe /online /get-packages.Problem is, those list only standard weekly, monthly, and stand-alone security updates.
What about updates to driver packages, Adobe Flash, HyperV software, VPN software, media players, and other 3rd party tools? The above commands will not help!
But what if you need to quickly identify machines who have not received proper patches from those 3rd party vendors? Those updates can be found in:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages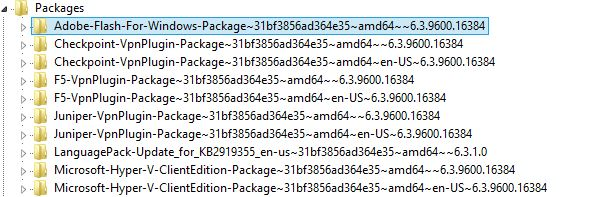
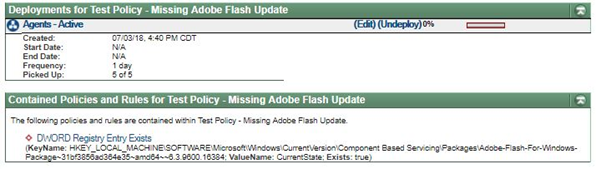
With ESP, locating on the network all machines with those missing packages can be as easy as creating a custom policy which checks for the presence or absence of the DWORD entries for those packages.
Once the machines who fail the check (and are therefore out of compliance with the policy) are identified, additional actions can be taken such as creating a more restrictive communication policy to be applied to those machines until the proper updates are detected.
In case your organization is tracking and measuring risk, all hosts who fail the update check can be flagged for higher risk status using ESP risk management features.
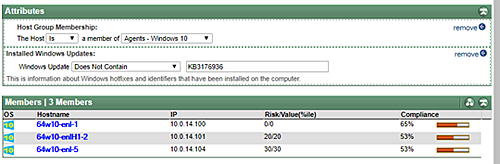
Verifiying that patches are indeed properly applied.
Depending on what software you use to distribute patches, verifying that a specific set of patches have been fully applied to all proper devices can be a challenge. ESP can help by providing effortless visibility into the network. For example, for Windows machines ESP automatically detects the patches that have been installed and those that are still pending installation. As a simple example, ESP can check which of the Windows 10 machines do not have update KB3176936. The machines that lack the update can be grouped together in a custom group for easy tracking. But what if it is a critical security update that patches up a high-risk vulnerability? The group can be assigned a certain risk coefficient and tracked more closely. If the vulnerability needs to be fixed right away, a custom policy could be created to prevent all machines in that group from accessing resources storing sensitive data, or to prevent them from communication on a certain range of ports, or to a certain range of IP addresses. Once the proper patch is applied to the machines, those restrictions will be removed automatically.