Protect Sensitive Data
ESP Case study: Protect sensitive data against compromise or loss
The Challenge
Enterprises face growing challenges to safeguarding their most critical assets - their confidential data and proprietary information. Hardening the network perimeter and carefully managing access to key servers and data stores helps prevent unauthorized intrusions. However, organizations still need to make confidential and proprietary information available for authorized users. Unless similar protections are pushed down to each and every machine that can access and handle this information, a significant potential remains for leakage.
The Solution
The Elemental Security Platform (ESP) provides a comprehensive solution for protecting enterprise data. ESP provides a policy and risk management based approach to assuring that only authorized users are granted access to data and that once accessed, the data is safe from misappropriation or tampering.
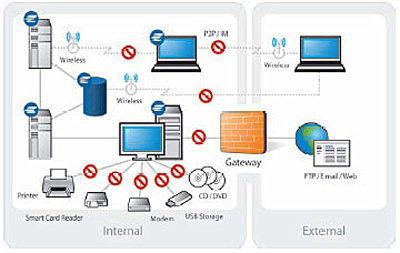
Controlling Access To Data
A key aspect of the ESP solution is policy-based access controls, which are continuously monitored at the host level to ensure only authorized users and machines have access to key information. Users and machines are grouped based on the current security posture of their computer, an assessment of the inventory and configuration of each machine, and a rich set of additional attributes that define the role each machine and user plays in the organization. The Elemental system continuously updates these groupings, controlling and monitoring access based on membership. This approach ensures that unauthorized machines - or those failing to comply with their assigned security policies - are denied access.
Protecting Data At The Point-of-Use
Once users have been granted permission to access information, policy-based controls enable control over each user's ability to redistribute or modify it. Security administrators can centrally define these policies, precisely target them, and automate deployment updates through Elemental's unique capability to dynamically group machines. This approach closely ties information protection measures with the access privileges that are granted. Once delivered to a machine, the policy controls are continuously implemented, whether or not the machine is connected to its local network.
Adapting To Change
The detailed visibility of users and machines provided by the Elemental system provides an automated policy management infrastructure that enables enterprises to easily manage policies for all communications on their networks. Policies are applied to groups of hosts or users, and automatically updated as changes in the state of machines or the activity of users is detected. IT staff can simply specify policies controlling access for groups of hosts or users that have the right to communicate, and whether either has the right to access protected resources.
Stopping The Leaks
Elemental provides a comprehensive suite of policies to shut down potential leaks. Key capabilities include:
- > Shutting Down Access To Writeable Media – Allows disabling of high-capacity local writeable storage devices such as USB memory sticks and CD/DVD burners. These policies can be implemented at all times, or on a more targeted basis (e.g., only when a user’s computer connects to a restricted network segment that contains isolated server and database machines).
- > Restricting Access To Printers – Enables local or networked printers to be disallowed. This mitigates the risk of users making hard copies of sensitive information.
- > Halting The Transfer Of Information Over The Network – Policies can be deployed that disallow file transfer applications such as instant messaging, P2P file sharing, and FTP file transfer. The unique ability to combine networking policies with host configuration and inventory policies within the same system at the data point-of-use reduces the risks of unauthorized transfer of data.
- > Preventing Data Leakage Via Email – Organizations commonly deploy mail filters to prevent proprietary information from getting out, but have little control over the private mail accounts of individual users. ESP lets administrators implement policy-based controls that limit this exposure, allowing users to communicate unencumbered through their corporate mail, while denying traffic bound for mail servers outside the perimeter.
- > Discovering Attempts By Unauthorized Applications To Use Approved Ports – The prevalence of legitimate Internet traffic in and out of enterprise networks makes it impractical to simply shut down Web access. However, the potential for applications to masquerade as Web traffic presents a significant risk. ESP allows administrators to implement policies that deny unapproved applications and their underlying processes from using port 80 or other network ports commonly allowed to traverse the perimeter.
- > Controlling Wireless Data Access – While few enterprises would give up the productivity gains furnished by wireless networking, it creates the potential for users to bypass many network security measures. Elemental's policy-based controls can shut down wireless access, or restrict it in terms of what machines a local computer can access over its wireless interface as well as what types of traffic are allowed in or out of the machine via wireless connections.
The Bottom Line
Information-based enterprises require a strong and multi-layered defense against compromise or unauthorized transfer of electronic information.
Today, the value of many organizations’ work product is more often manifested as electronic data (information and intellectual property) than as tangible assets. This makes enterprise security officers accountable for safeguarding the enterprise’s most valuable assets. At the same time, governments and other bodies are regulating measures to prevent the compromise or disclosure of non-public information, and no security officer wants to be responsible for a security breach that becomes the next front page story in the business news.
Protecting information has become a paramount concern for organizations of all types. ESP ensures the proper and continuous implementation of policies that protect information. By bringing together an end-to-end solution for securing access to data in motion and ensuring the integrity of data at rest, Elemental enables organizations to be assured that their information is secure while giving them the flexibility they need to function effectively in an increasingly connected and information-centric world.
Click here to request more information or an online demo
